As an Amazon Associate, I earn from qualifying purchases. This means I may earn a small commission if you use my affiliate links, but there's no extra cost for you!
If you have visited my blog recently, you may have unexpectedly stumbled upon a disturbing blog post; it wasn’t my doing, Stacey in the Sticks had been hacked! I wasn’t alone in this; many fellow bloggers suffered the same fate, with very similar posts. I won’t lie, it was very scary and panic inducing. I thought I had lost a whole post that had taken me a while to prepare and write; but any post written would have had the same effect.
To know that somebody had immersed themselves into my world, potentially stolen my data, and imposed their beliefs on my blog and my readers; it was horrible. By imposing their beliefs, this is what I mean (apologies for the unsavoury language, but I wanted a clear picture of exactly what happened):
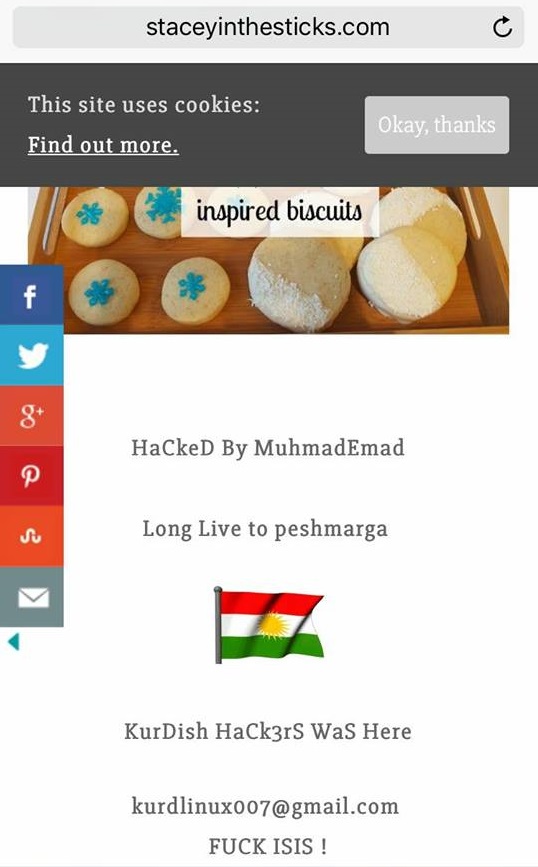
Not nice, right? When you have taken years of hard work to build up your brand, and then this happens. I cannot stress enough how much it stressed me out. Luckily enough, this was a simple fix to get my original post back. There are obviously many other ways and means that hackers work, and this is just in the minority; though it’s the first time I’ve ever been a victim of hacking. It did get me wondering though, am I protecting myself enough?
There are many ways in which you protect yourself from data transfer hacks and Data Label have put together this handy guide with some steps you can take to make sure your data is kept secure. Admittedly I don’t do all of these already, but I did immediately change all of my passwords again; something which I do regularly anyway. I make sure I back up my blog every month too using BackupGuard, and continually save drafts as I am writing; luckily I was able to retrieve my blog post this way! If you think you may have been hacked, you can also use a tool such as Kaspersky to run a virus & malware check.
Taking these steps may not completely stop data transfer hacks, but they will go a way to helping you retrieve your data if you are ever unlucky enough for it to happen.
Have you ever been a victim of hacking in any way?
*PR collaboration
Amazon and the Amazon logo are trademarks of Amazon.com, Inc, or its affiliates.

